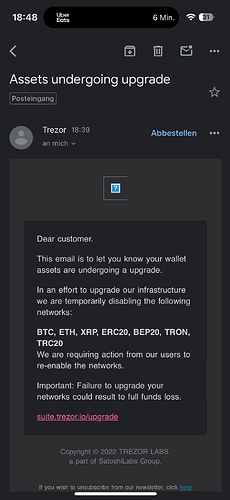
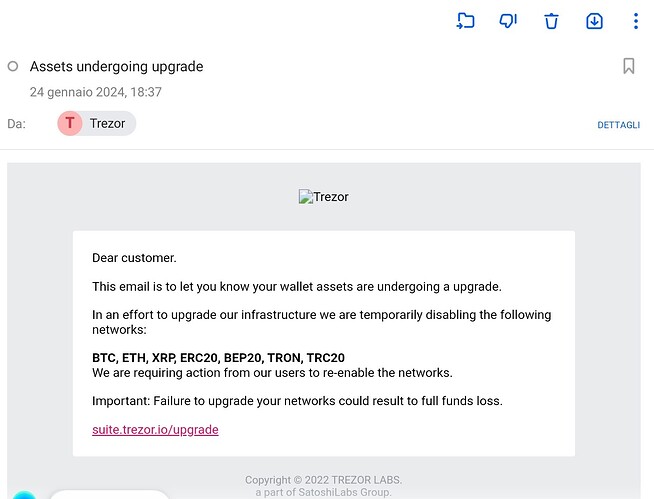
Just wanted to inform you about this phishing email I just got
i have just received the exakt same email.
interestingly to an email address i have only used to buy my trezor device (and where i do receive occasional newsletters). i can tell that for sure, since i create specific unique email addresses for any of the many services i use.
from my understanding, this emal address can’t have been leaked via the ticketing systems breach, since i never opened a support ticket.
also interesting: all the links in that email do look legit; for example the suspicious upgrade links reads in full: r_mailing_trezor_io/mk/cl/f/sh/7nVU1aA2nfsTTJuSASLvyu3UqAr02wG/nx4F2jkSeX0D
(replaced the dots by underlines)
Yes I just received the same email.
Smelled a bit phishy!
Please confirm if actually legit…
Same here.
What they ask made no sense to me:
Failure to upgrade your network could result to full funds loss… stupid phishing guys
I got the same phishing email also, today.
Hello, this is clear phishing attempt, mark as spam and follow the standard security practices. We are already investigating.
There is a big pinned banner on the forum informing about this possibility.
Though we have not observed any spike in phishing activity as a result of this incident, in our commitment to full transparency, we have decided to alert you to phishing schemes targeting your recovery seed.
What you should know:
![]() Your Trezor wallet and assets remain secure
Your Trezor wallet and assets remain secure
![]() NEVER share your recovery seed with anyone. Remember, Trezor representatives will never prompt you to do so
NEVER share your recovery seed with anyone. Remember, Trezor representatives will never prompt you to do so
![]() Be cautious of phishing attempts or suspicious emails
Be cautious of phishing attempts or suspicious emails
![]() Always confirm instructions directly on your Trezor device
Always confirm instructions directly on your Trezor device
… since this follows the usual scheme (“click her or you loose funds”) it’s pretty obvious; i’d be still keen to know how a phising attempt could work, that uses an url derived from an *.trezor.io subdomain?
This attack is quite serious they are using the subdomain: r.mailing.trezor .io
did they manage to hack trezor‘s domain?
I have received the same email and did some research. Note: I am a security analyst.
It looks like the email came from Trezor’s own Sendinblue account. Sendinblue is an email marketing platform that Trezor uses for its newsletters. There is a very high chance this account has been compromised.
Why do I believe this? SPF, DMARC, and DKIM all checked out on the email, which means it was sent from Trezor’s own Sendinblue account.
I tried attaching some screenshots to this post, but unfortunately, as a new forum member, I wasn’t allowed to do so.
I have emailed Trezor support with all my findings.
The problem with this email is that it passed DKIM email signing meaning your DKIM signing keys are compromised
Return -Path: <[email protected]>
**Authentication-Results: perfora.net; dkim=pass [email protected]**
Received: from mailing.trezor.io ([172.246.19.223]) by mx.perfora.net
(mxeueus005 [74.208.5.3]) with ESMTP (Nemesis) id 1MQMFJ-1rfZ9V1ZJp-00LvZM
for <[email protected]>; Wed, 24 Jan 2024 18:32:00 +0100
DKIM-Signature: a=rsa-sha256; bh=05Czb/5OSEWG9K/kXg0Y0iWfbbgktylX3HS52KP3Lyc=;
c=relaxed/relaxed; d=trezor.io;
h=to:cc:from:reply-to:subject:date:mime-version:content-type:list-id:list-unsubscribe:x-csa-complaints:list-subscribe-post:message-id:sender:x-sib-id:x-mailin-client:x-mailin-campaign:feedback-id;
q=dns/txt; s=mail; t=1706117518; v=1;
b=FoJeA8CSpQtgeQXy6CQQgu7KQUh6p7mokwZ6/EPRdBmkAITETOb2hmsNFhtJ7Gg8vbwvTkZS
cgJbFJUwAuF21bRIB9tcKmacxA3Nsh/YAPXvZr6VNiPINckdUKhht1u6xuUwxpOlGanm0fwc+Te
5Jqxd6wPEOE8VKP1iwwINM0g=
this would also explain, why i received that email at all. i can confirm that the particular (unique) email address was only ever used to buy my device and to receive the trezor newsletter…
I would like to back this by hinting to the unsubscribe URL at the end of the email. It looks almost exactly like the unsubcribe URL from the legit mailings:
trezor mailing url/mk/un/sh/7nVT[truncated]iRWFA/yESPeq6k_ud…
trezor mailing url/mk/un/sh/7nVT[truncated]iRWFA/wccHfsguPzo…
It’s more likely “just” their Sendinblue account. Which is kind of shocking, given that just recently their support ticket system was also compromised and then used for phishing emails.
The problem is the support ticketing portal still being compromised and used to send out the phishing mails and host the page for harvesting user wallet seed inputs
This is coming from their newsletter account (Sendinblue) though, not from the support portal. It looks like they have another compromised account at their hands.
The sub domain is “r” “mailing” trezor dot io
Don’t forget to tell your parents and grandparents and relatives who are tech challenged to not fall for this. I helped my Mom get on trezor and I know she would fall for this.
I concur with John_DC, MX/SPF, header analysis, etc. confirm email coming from a valid source, meaning account within trezor compromised and sending this email.
Did notice one difference in the account sending from previous valid accounts though.
There is no hyphen in this noreply@, usually its no-reply@…