### Actual behavior
I run few masternodes on Allnodes.com, get the rewards to… be sent to other payee addresses which are in my Trezor-Electrum wallet.
Things have gone well for the last 5 months, until yesterday. There was one reward that already got 230+ confirmation, but still I could not send it out. This error message appeared right after I pressed confirm on my Trezor.
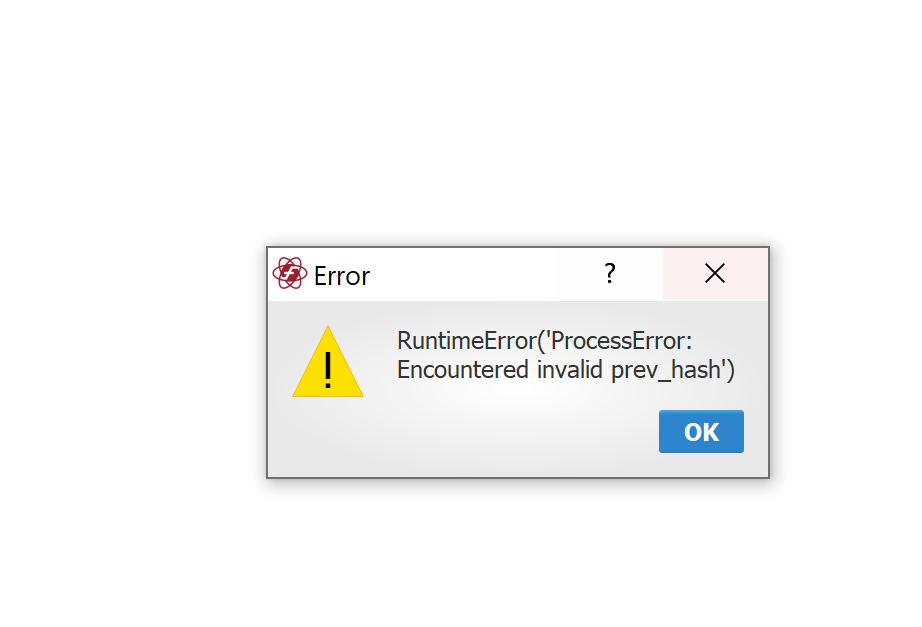
The rest of the rewards are OK.
Wallets, Trezor HWs and laptops that I tried :
Wallet : Electrum 4.0.9.4
Trezor T firmware 2.4.0
Trezor One firmware 1.10.0
Laptops : 2 different laptops, running both Win 10 Pro version 20H2

### Crash / debug logs
<!-- Please run it with -vdebug with a terminal and paste the important exerpts from the output here.
Linux: cd to the install dir, run `python3 run_electrum -vdebug`
MacOS: Mount the image, cd to the mounted volume, find the app (find . -name "Electrum-XZC"), execute PATH/Electrum-XZC -vdebug. For example `cd /Volumes/Electrum-XZC; Electrum-XZC.app/Contents/Macos/Electrum-XZC -vdebug`
-->
Microsoft Windows [Version 10.0.19042.1165]
(c) Microsoft Corporation. All rights reserved.
C:\Program Files\Firo Electrum>console-electrum-firo-4.0.9.4.exe -vdebug
I | logging | Firo Electrum version: 4.0.9.4 - https://electrum.dash.org - https://github.com/firoorg/electrum-firo/
I | logging | Python version: 3.7.9 (tags/v3.7.9:13c94747c7, Aug 17 2020, 18:58:18) [MSC v.1900 64 bit (AMD64)]. On platform: Windows-10-10.0.19041-SP0
I | logging | Logging to file: None
I | logging | Log filters: verbosity 'debug', verbosity_shortcuts ''
I/p | plugin.Plugins | registering hardware digitalbitbox: ('hardware', 'digitalbitbox', 'Digital Bitbox wallet')
I/p | plugin.Plugins | registering hardware keepkey: ('hardware', 'keepkey', 'KeepKey wallet')
I/p | plugin.Plugins | registering hardware ledger: ('hardware', 'ledger', 'Ledger wallet')
I/p | plugin.Plugins | registering hardware safe_t: ('hardware', 'safe_t', 'Safe-T mini wallet')
I/p | plugin.Plugins | registering hardware trezor: ('hardware', 'trezor', 'Trezor wallet')
D/T | util.profiler | Plugins.__init__ 0.0000
I/n | network | blockchains [0]
I/D | dash_net.DashNet | failed to load banlist.gz: FileNotFoundError(2, 'No such file or directory')
I | exchange_rate.FxThread | using exchange CoinGecko
D/T | util.profiler | Daemon.__init__ 0.1008
I | daemon.Daemon | launching GUI: qt
I/n | network | starting network
I/n | network | setting proxy None
I | daemon.Daemon | starting taskgroup.
I/n | network | connecting to electrumx01.firo.org:50002:s as new interface
I/n | network | starting taskgroup.
I | gui.qt.history_list | could not import electrum_firo.plot. This feature needs matplotlib to be installed.
I | gui.qt.ElectrumGui | Qt GUI starting up... Qt=5.14.2, PyQt=5.14.2
D/T | util.profiler | ElectrumGui.__init__ 0.1607
I | storage.WalletStorage | wallet path c:\users\admin\appdata\roaming\electrum-firo\wallets\house 2 reward
I | storage.WalletStorage | wallet path c:\users\admin\appdata\roaming\electrum-firo\wallets\house 2 reward
I/i | interface.[electrumx02.firo.org:50002] | connection established. version: ['ElectrumX 1.16.0', '1.4.2']
I/i | interface.[electrumx02.firo.org:50002] | set blockchain with height 401944
I/i | interface.[electrumx02.firo.org:50002] | could connect 401945
I/n | network | no height for main interface
I/n | network | fee_estimates {25: 9082, 10: 9082, 5: 9082, 2: 9082}
I/p | plugin.Plugins | loaded digitalbitbox
I/p | plugin.Plugins | loaded keepkey
I/p | plugin.Plugins | loaded ledger
I/p | plugin.Plugins | loaded safe_t
I/p | plugin.Plugins | loaded trezor
I | plugin.DeviceMgr | scanning devices...
I/i | interface.[electrumx01.firo.org:50002] | connection established. version: ['ElectrumX 1.16.0', '1.4.2']
D/T | util.profiler | DeviceMgr.scan_devices 0.0386
I | plugins.trezor.qt.Plugin | connecting to device at bridge:16
I | plugins.trezor.qt.Plugin | connected to device at bridge:16
I/i | interface.[electrumx03.firo.org:50002] | connection established. version: ['ElectrumX 1.16.0', '1.4.2']
I/i | interface.[electrumx01.firo.org:50002] | set blockchain with height 401945
I/i | interface.[electrumx01.firo.org:50002] | skipping header 401945
I/n | network | no height for main interface
I/n | network | switching to electrumx02.firo.org:50002:s
I/i | interface.[electrumx.firo.org:50002] | connection established. version: ['ElectrumX 1.16.0', '1.4.2']
I/i | interface.[electrumx03.firo.org:50002] | set blockchain with height 401945
I/i | interface.[electrumx03.firo.org:50002] | skipping header 401945
I/n | network | fee_histogram []
I/i | interface.[electrumx.firo.org:50002] | set blockchain with height 401945
I/i | interface.[electrumx.firo.org:50002] | skipping header 401945
I/n | network | fee_estimates {25: 9082, 10: 9082, 5: 9082, 2: 9082}
I/n | network | fee_estimates {25: 9082, 10: 9082, 5: 9082, 2: 9082}
I/n | network | fee_estimates {25: 9082, 10: 9082, 5: 9082, 2: 9082}
I | plugin.DeviceMgr | Registering Pepe Bitrock/8A088217255D0E7E0ADB5A6A
I | plugin.DeviceMgr | scanning devices...
D/T | util.profiler | DeviceMgr.scan_devices 0.2516
D/T | util.profiler | WalletDB._load_transactions 0.2511
D/T | util.profiler | AddressSynchronizer.load_local_history 0.0312
D/T | util.profiler | AddressSynchronizer.check_history 0.0156
I | synchronizer.[house 2 reward] | receiving history aHu1Bhm2kBtunNUrbr81CndZ9rLiubMnQy 12
I/w | wallet.Standard_Wallet.[house 2 reward] | set_up_to_date: True
I | storage.WalletStorage | saved c:\users\admin\appdata\roaming\electrum-firo\wallets\house 2 reward
D/T | util.profiler | WalletStorage.write 0.2865
I | verifier.[house 2 reward] | requested merkle ad10a600c11ffb2d6bf1adf6a0b63fa1290a3d218b122d909545ed2183775aa0
I | plugin.DeviceMgr | scanning devices...
D/T | util.profiler | Deterministic_Wallet.try_detecting_internal_addresses_corruption 0.0016
D/T | util.profiler | ElectrumWindow.load_wallet 0.2212
I/w | wallet.Standard_Wallet.[house 2 reward] | set_up_to_date: False
I | synchronizer.[house 2 reward] | receiving history aFsqAWye67kud7NRoGr2tTuPb37biqiANi 410
I | verifier.[house 2 reward] | verified ad10a600c11ffb2d6bf1adf6a0b63fa1290a3d218b122d909545ed2183775aa0
D/T | util.profiler | DeviceMgr.scan_devices 0.3877
I | plugin.DeviceMgr | getting client for keystore
I/w | wallet.Standard_Wallet.[house 2 reward] | set_up_to_date: True
I | plugin.DeviceMgr | end client for keystore
I | plugin.DeviceMgr | getting client for keystore
I | plugin.DeviceMgr | end client for keystore
I | storage.WalletStorage | saved c:\users\admin\appdata\roaming\electrum-firo\wallets\house 2 reward
D/T | util.profiler | WalletStorage.write 0.2910
I | gui.qt.history_list.HistoryModel | refreshing... reason: update_tabs
D/T | util.profiler | HistoryModel.refresh 0.0000
D/T | util.profiler | Abstract_Wallet.get_full_history 0.2193
D/T | util.profiler | HistoryModel.process_history 0.0000
D/T | util.profiler | UTXOModel.get_coins 0.3530
D/T | util.profiler | HistoryModel.process_changes 0.0321
D/T | util.profiler | UTXOModel.process_changes 0.0000
D/T | util.profiler | UTXOModel.refresh 0.0000
D/T | util.profiler | AddressModel.get_addresses 0.0000
D/T | util.profiler | AddressModel.process_changes 0.0000
D/T | util.profiler | AddressModel.refresh 0.0000
D/T | util.profiler | UTXOModel.process_changes 0.0000
D/T | util.profiler | UTXOModel.refresh 0.0150
I | storage.WalletStorage | saved c:\users\admin\appdata\roaming\electrum-firo\wallets\house 2 reward
D/T | util.profiler | WalletStorage.write 0.3001
I | plugin.DeviceMgr | getting client for keystore
I | plugin.DeviceMgr | scanning devices...
D/T | util.profiler | DeviceMgr.scan_devices 0.3015
I | plugin.DeviceMgr | end client for keystore
I | plugin.DeviceMgr | getting client for keystore
I | plugin.DeviceMgr | scanning devices...
D/T | util.profiler | DeviceMgr.scan_devices 0.4039
I | plugin.DeviceMgr | end client for keystore
I/n | network | fee_estimates {25: 9082, 10: 9082, 5: 9082, 2: 9082}
I/n | network | fee_histogram []
I/n | network | fee_estimates {25: 9082, 10: 9082, 5: 9082, 2: 9082}
I/n | network | fee_estimates {25: 9082, 10: 9082, 5: 9082, 2: 9082}
I/n | network | fee_estimates {25: 9082, 10: 9082, 5: 9082, 2: 9082}
E | gui.qt.main_window.[house 2 reward] | on_error
Traceback (most recent call last):
File "electrum_firo\plugins\trezor\clientbase.py", line 257, in sign_tx
File "trezorlib\tools.py", line 231, in wrapped_f
File "trezorlib\btc.py", line 263, in sign_tx
File "trezorlib\tools.py", line 231, in wrapped_f
File "trezorlib\client.py", line 223, in call
trezorlib.exceptions.TrezorFailure: ProcessError: Encountered invalid prev_hash
The above exception was the direct cause of the following exception:
Traceback (most recent call last):
File "electrum_firo\gui\qt\util.py", line 848, in run
File "electrum_firo\wallet.py", line 1446, in sign_transaction
File "electrum_firo\plugins\trezor\trezor.py", line 96, in sign_transaction
File "electrum_firo\plugin.py", line 362, in wrapper
File "electrum_firo\plugin.py", line 355, in run_in_hwd_thread
File "concurrent\futures\_base.py", line 435, in result
File "concurrent\futures\_base.py", line 384, in __get_result
File "concurrent\futures\thread.py", line 57, in run
File "electrum_firo\plugins\trezor\trezor.py", line 345, in sign_transaction
File "electrum_firo\plugin.py", line 362, in wrapper
File "electrum_firo\plugin.py", line 352, in run_in_hwd_thread
File "electrum_firo\plugins\trezor\clientbase.py", line 257, in sign_tx
File "electrum_firo\plugins\trezor\clientbase.py", line 85, in __exit__
RuntimeError: ProcessError: Encountered invalid prev_hash